“Quantum computers may still be years away, but the shift toward quantum-safe cryptography is happening now — driven by regulation, long-term risk, the risk of harvest now-and-decrypt-later, and the growing cost of secure communication.”
For a long time, cryptography has quietly underpinned financial, government and enterprise systems, consuming relatively little compute and rarely entering strategic discussions. That era is ending.
The transition to post-quantum cryptography (PQC) — accelerated by government requirements and emerging security risks — will fundamentally change the computational profile of secure communication. Symmetric data encryption algorithms is largely considered Quantum Safe with longer keys, but the asymmetric algorithms used for exchanging the symmetric keys are not.
Organizations that depend on encrypted data flows are now confronting a new reality: the cryptographic layer is becoming a performance factor in its own right.
Why Invest Before Quantum Computers Exist? Two Reasons: Regulation and Risk
1. Government regulations require preparation now
Across the U.S., EU, and Asia, new frameworks mandate:
- cryptographic inventory
- migration planning
- crypto-agility
- PQC readiness
Long before quantum computers can break encryption, regulators require enterprises to ensure that their systems will be safe when the time comes.
2. “Harvest now, decrypt later” is already happening
Adversaries are collecting encrypted traffic today with the intention of decrypting it in the future using quantum capability.
This means sensitive data with a long lifespan — financial records, identity data, government communications — is at risk right now, even if encryption appears safe today.
This is why PQC is more than a future problem.
It is a present-day planning and risk management issue.
Software Alone Won’t Be Enough — And Enterprises Are Starting to Realize It
Many organizations assume that open-source software like OpenSSL will absorb PQC requirements for years.
But PQC introduces heavy performance penalties:
- much larger public keys
- heavier signature verification
- longer key-exchange operations
- hybrid modes that double cryptographic work doing both old world and new world cryptography
- multiplied load across API gateways, microservices, and secure sessions
This sudden shift pushes CPU-based cryptography beyond practical limits in large-scale environments. Even with optimized software, enterprises will face:
- higher energy consumption
- more servers to maintain throughput
- unpredictable latency during load spikes
- increased operational costs
This is where hardware acceleration becomes relevant — not as a replacement for software, but as a strategic boost to maintain performance and TCO.
Where Silicom SACA Fits — A Seamless Boost to the Software Path Enterprises Already Trust
Silicom’s SACA accelerator was designed specifically for this transition.
It is not an infrastructure overhaul.
It is not a proprietary ecosystem.
Instead, it integrates directly with OpenSSL 3.5 and support hybrid QAT/SW/SACA environments — the same tools enterprises will use in their PQC migration anyway.
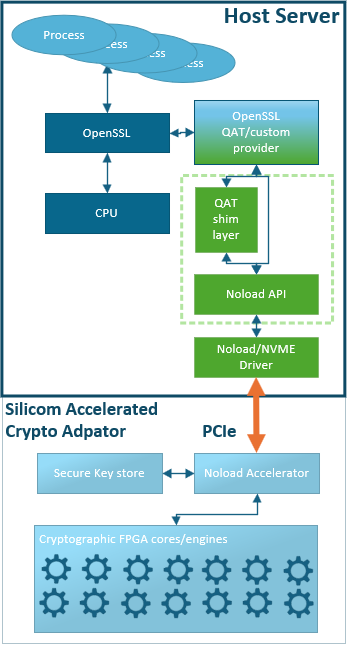
SACA acts as a transparent offload engine for both classical and post-quantum cryptography, allowing software teams to continue using familiar libraries and workflows.
Key advantage:
SACA allows enterprises to adopt PQC without paying the full CPU and energy cost of PQC in software. Even for existing systems , can benefit greatly if they are currently relying on SW on CPU or even QAT for its crypto offload. Here QAT HW offload does not support PQC operations and the added PQC requirements can only be met by CPU or SACA HW offload. These CPU systems are not geared for heavy crypto operations but rather its business application. SACA extends the life and capabilities of these systems into a world dominated by post quantum cryptography, at minimal CPU and power resources.
The Performance Gap Is Too Large to Ignore
In internal validation, SACA delivered:
✪ 450,000 hybrid PQC handshakes/sec (X25519ML-KEM768)
✪ Offloaded work equivalent to 85+ CPU cores
For pure PQC like KEMTLS the gap between CPU and SACA offloading is even greater. This demonstrates a simple truth: PQC algorithms with long keys and heavy math do not scale well on CPUs.
Enterprises need hardware assistance — not eventually, but as part of their migration path.
A Real-World Example: High-Volume Secure Connections
In environments such as secure customer platforms, CDNs, banking APIs and large identity systems, connection establishment dominates cryptographic load. With SACA deployed with an Altera® Agilex™ AGF014 (midrange) FPGA:
- up to 150,000 ECC-based connections/sec can be offloaded
- for hybrid PQC handshakes it delivers nearly double of this throughput
- CPU load can be reduced by up to 85%
- system power consumption for crypto operations can drop by 70%
- hardware footprint and TCO decrease significantly
These benefits matter long before full PQC deployment — they improve performance today while preparing infrastructure for PQC tomorrow.
Conclusion: PQC Is a Journey — SACA Makes the Transition Practical
Banks, exchanges, and enterprises face a critical shift: cryptography is becoming heavier, more frequent, and more regulated. Quantum computers may not be here yet, but:
- regulations are
- risks are
- and the performance burden is growing
SACA provides a practical, software-compatible way to absorb this transition — reducing cost, stabilizing performance, and enabling a smooth migration to quantum-safe cryptography without disrupting existing systems.
Despite being hardware based the nature of the FPGA makes it fully reprogrammable ensuring future in-field upgrade paths and allows for new algorithms. Unlike ASIC based technologies.
The organizations that plan early will be the ones best positioned to meet the next decade of security requirements — without compromising performance or efficiency. These organizations will also be at the forefront when government agencies look to upgrade their systems for PQC compliance.
Interested in learning more about Silicom SACA solution?
We’d be happy to continue the conversation—feel free to reach out to our teams to explore how this powerful hardware-based cryptographic acceleration platform can accelerate your next project.